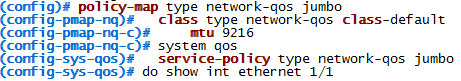
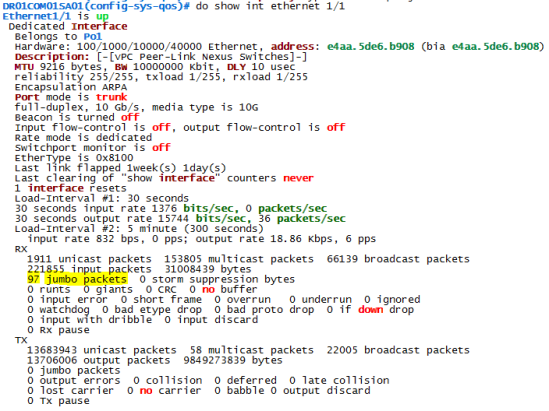
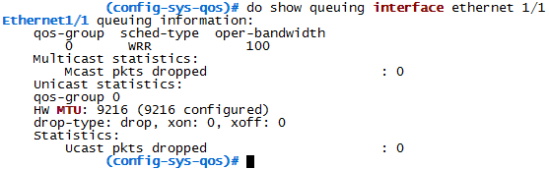
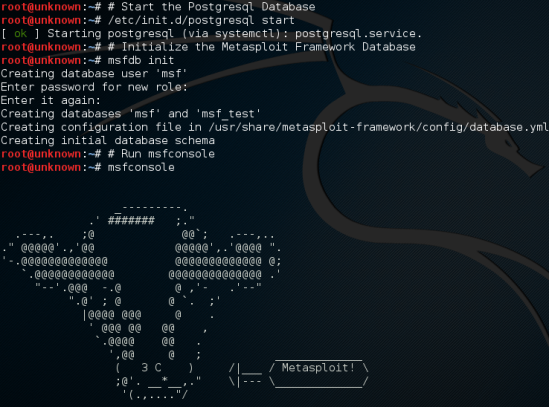
If you are sick and tired of the old green/black or black/white themes (white/dark blue in my case) like I was, you starting looking alternatives…
I have found a page that uses a little .ini file to customize Cisco words with colours (also does a great job on Juniper)!
Unfortunately, I cannot find it again to post the direct link, but all the credits goes to this unknown blogger.
The outcome will be this:
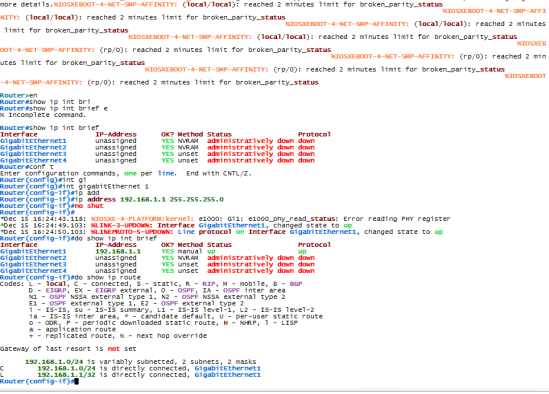
Steps:
- Download “Cisco Words.ini” File here
- Search for the installation folder of SecureCRT, and copy the file into folder Config\Keywords.

Note: You can check on Global Options -> Configurations Paths
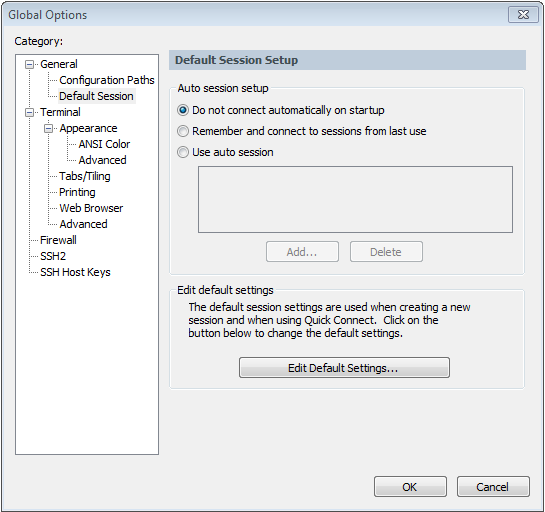
- Go to Options -> Global Options..
- Select Default Session -> Edit Default Session…
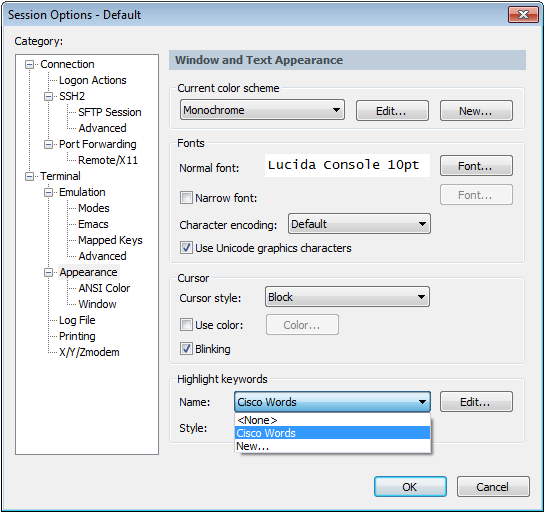
- Terminal -> Appearance -> Highlight keywords -> Name and Select “Cisco Words”
After this, you will be ready to see the terminal with a new pair of eyes!